It seems not a day goes by without some record cybersecurity incident hitting the press, be it a data breach, a Zero Day or some malware doing its devious things… Trouble is the frequency of these events, and their scope, has been increasing significantly over the last few years and most people have not latched onto how big the problem is.
A recent Statista Market Insights survey predicts that the cost of cyberattacks in 2024 could likely reach $9.2 trillion across the globe. To put it in context that is more than the 2022 GDP of Japan and Germany combined. This is triple the figure of $2.95 trillion in 2020, a short 4 years ago.
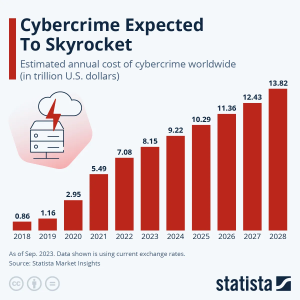
This is clearly outpacing the growth of the global economy, so the ability to enact profitable cybercrime at scale must be getting easier and more rewarding. There is no other way to interpret such a dramatic increase in the rewards of cybercrime, they are getting away with it more often and being well rewarded for their efforts.
Why is this happening?
There is a confluence of factors which are coming together and contributing to cybercrime growth:
- Increased system complexities and interconnectedness: Over the last few years there has been an explosion in cloud services and connected devices, both in the home and office. Nearly every IT device you buy now comes with some ‘cloud’ service offering – be that remote access to just simple backup services. This has created an explosion in the complexities of the associated surfaces to secure. Long gone are the days when you just needed to secure your office network, now you need to secure a smorgasbord of cloud services to operate even the smallest business; and in most cases the businesses just don’t have the time or resources to be able to do that. The same can also be said for a lot of large businesses as well – the security complexity in IT can quickly get away from you.
- Invisible dependencies: Associated with the above are ‘Russia Doll Dependencies’, in that a service quite often depends on another service, which depends on another service, etc, etc.. In other words what you see of a service hides a massive tree of dependencies which can end up spanning the whole globe, and most of those dependencies are beyond your awareness and control. Good luck ensuring all of that remains secure 24×7.
- Fire and forget security solutions: The knee jerk reaction by most companies has been to go on a spending spree to buy off-the-shelf security solutions, set them up once and promptly forget about them. This may make them feel happy that they think they are secure, but refer back to the 2 prior points, 99.9% of the business security surface is beyond your control. Plus once this off-the-shelf security solution is forgotten about, it will often be not maintained or the licence for its operation will expire and it will silently stop working.
- Insecure default configurations: Literally everything comes with terrible security defaults, and we wonder why admin/admin is still one of the most common device logins going. Plus by default logging is often turned off or does not exist, or some remote UPnP pops into existence on a ‘just in case we need to get in remotely’ basis.
- Its easy to hack: There is a wide range of ‘hacking’ or ‘ransomware-as-a-service’ toolkits out there, you don’t need to be a cyber-ninja nowadays to make hacking pay, just be willing do it. The level of technical skill is actually quite low.
- The hackers are more organised: There is a lot focus on doing hacking as a business enterprise, this creates economies of scale for all hackers and grows an underground community.
- We like hanging onto sensitive information: Businesses (and individuals) have a tendency to either keep information on a just-in-case basis or they just plain forget what information they have. Combine this with operating systems that do absolutely nothing to manage data lifecycles and files just accumulate all over the place. You would be horrified what most people have in their inboxes, documents folder or shared corporate drive. Everything from passport images upwards in sensitivity.
- Confusion over regulations and what data must be kept: businesses are often not sure what they need to keep to protect themselves or to comply with regulations within the sectors they operate in, so they often keep everything…
Now, you may think one big factor in all of this has being missed, the shortage of those with cybersecurity skills, but this is becoming a bit of an excuse rather than a reason. Let me explain why:
- We are always going to be short of good people in cybersecurity: The simple reason being to do it well requires a certain ‘mindset’ and depth of experience – you can’t get that straight out of Uni or TAFE. You need to be able to worry about what really matters and ignore the rest; a lot of people fret over everything and that doesn’t work. You also need to know dependable techniques that deal with human factors (which are covered in a lot of articles on this site BTW).
- Cybersecurity really is a concern for everyone: Pointing the finger at cybersecurity professionals is wrong, everyone needs to up their security game and the facilities need to be provided to allow this to happen.
- The complexity & dependency super explosion: Refer back to the first 2 points on the first list, do you think throwing more manpower and technology (including AI & all that implies) is going to do anything to meaningfully change the situation? When you are faced with an exponential growth in interconnectedness and complexity, no amount of manpower or technology will cover it.
So what is the solution? There are multiple problems that need solving right now:
- Reign in the interdependencies: Not only are multiple levels of dependency a security nightmare, its also a maintenance nightmare as well. Plus you could be dependent on a whole web of hidden companies and individuals to maintain and provide secure and reliable (and bug free) services. This is not a viable long term arrangement; businesses change direction or close down, people move onto other things, versions are retired, etc. If you don’t manage your dependencies, they will end up managing you.
- Data lifecycle support baked right into the base: Its 2024 and applications engineers are still expected to code up data lifecycle support. Anything stored in a disc or database should be able to be tagged with a ‘delete on’ timestamp and when that time arrives, its automatically removed. In essence this should be an atomic operation at the Operating System and Database level – stop putting it all on the developer to worry about this.
- Do you really need that data? As hinted at above individuals and businesses need to be a lot more wary of holding onto data; if they have no specific need for it, just delete; or even better don’t collect it in the first place. Training should be provided on this. Hackers almost depend on this tendency to accumulate data to make ransomware and data breach attacks effective; if you didn’t have valuable data, there would be nothing to gain.
- Do more with less: There is a trend developing of needing every little tool or service out there to do your work. Quite a few people have their set of favourite tools or services and want to take that set with them from job to job. Trouble is, with all the cloud connections and dependencies, this creates a management nightmare for both the IT and Security departments in a business (if you are large enough to have these to begin with). It also inefficiently consumes resources and is a distinct cost to manage. Plus everyone else will need to adapt to the differences, creating yet more inefficiency. Of course this also creates a massive security headache. The solution? Have a prescribed list of supported and approved services, anything not on that list cannot be used, this is controlled jointly by IT/finance and security. Also make sure you are not doubling up on functionality with anything on that list.
- Examine what needs to be local or remote: The usage of cloud services needs to be considered against the criticality of those services and who they are for. Customer facing services need to be in multiple deployments and isolated completely from your office, so cloud fits. But does a purely internal service or data store also need to be in that same cloud service? Could a local virtualising server run such a service? (yes, with remote secure backups of course). The world of containers and associated support frameworks makes it much easier to run local services. Yes, you need to have some hardware and its an additional machine or two for IT to support, but you retain full control; which could be ideal for certain business functions. The technology cloud providers use to scale servers is now available for local hosting functions as well, you can create a local compute cluster for quite a reasonable price. Remember the cloud providers have to extract profit from the services they provide and you get no access to depreciation or R&D equipment write offs if you use them.
- Give everyone security training: Cybersecurity is not just a ‘geeky’ thing, everyone is touched by it, so everyone should get security awareness training. Be it the front desk receptionist to the software developer & CEO, everyone has a role to play in maintaining security and you cannot expect them to deliver on that without training, in exactly the same way you need training to drive a car safely.
Conclusion
The drastic increase in the value of cybercrime is more a reflection of how our usage of technology is ahead of our collective security skills. We utilise more interconnected services than ever before and that leaves behind a massive data lake that we are constantly contributing to, just sitting there for criminals to plunder at our collective expense. We need to recognise this for the problem it is, rethink our approach on many levels and adapt. This may seem like a ‘moon shot’ scale problem, but we have been able to do it once, I’m confident we can do it again.